Running Line of Business web apps on the intranet is a common requirement. This article series explores how to do so while leveraging Azure App Service and its capabilities.
For a while, using the ASE was the only way to run an App Service in a private VNet. App Service support for Private Endpoints became generally available (GA) in all regions in October 2020, making it a cost-saving alternative to explore. In July 2021, ASE v3 also became GA and no longer has a stamp cost. Let’s take a quick look at both service offerings.
App Service Environment (ASE)
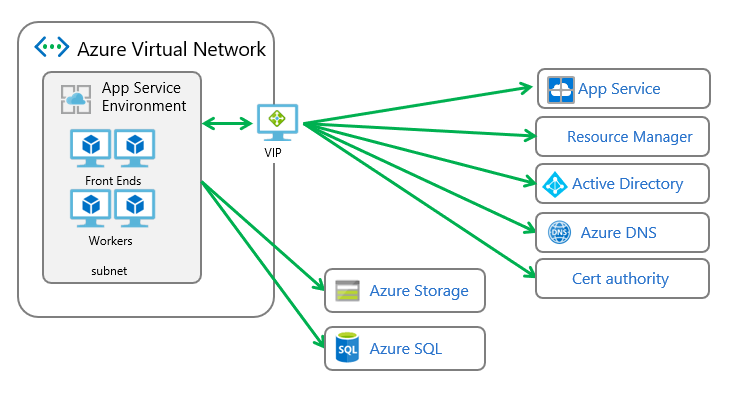
The ASE is a single-tenant deployment of the Azure App Service into a VNet with a fine grain control over inbound and outbound traffic offered by an NSG. It comes with its own Isolated pricing tier.
There are two flavors of it:
- Internal facing with an internal load balancer IP, ILB ASE
- Internet-facing with a public VIP, External ASE.
Both types have a public VIP used as the source for the outbound calls within the ASE and inbound management calls. The outbound calls made inside the VNet or over the VPN will have the source IP, a private IP from the VNet range.
Internal Load Balancer ASE (ILB ASE)
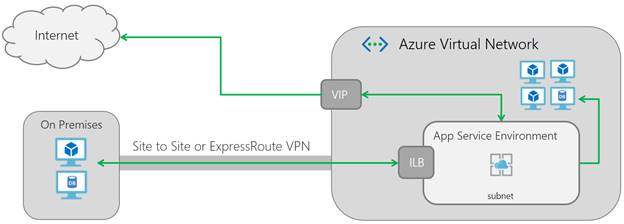
For the ILB ASE, the internal endpoint is an internal load balancer, hence the naming. There is also the possibility to expose the ILB ASE to the internet by safely putting it behind an Application Gateway (WAF).
External ASE
Azure Private Link
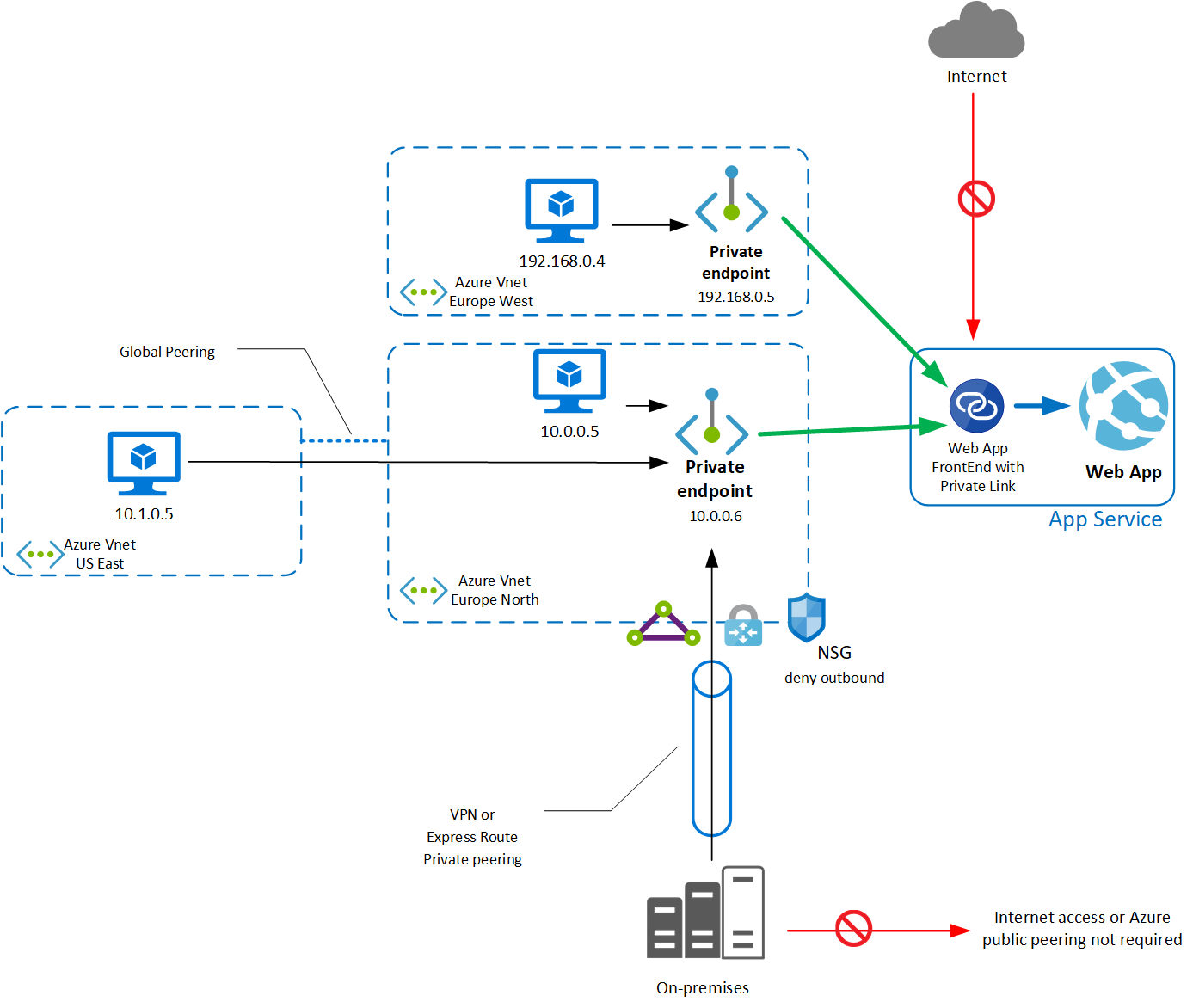
This service enables private access to Azure PaaS Services or custom services by mapping them to a Private Endpoint inside a VNet, with no need for a public IP. Then, these services can be accessed through the Private Endpoints, from on-premises over ExpressRoute or VPN, also from the same VNet and regional or globally peered VNets.
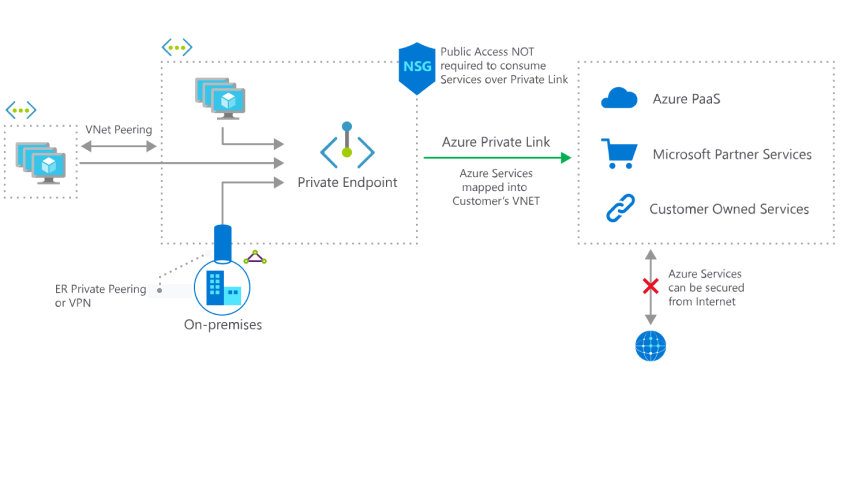
The traffic between the private endpoint and the service travels over the Microsoft backbone network. Custom services can also use the Private Link service by being placed behind a Standard Load Balancer. Both consumers and the exposed services can be in different AAD tenants, subscriptions, regions. Also, there can be multiple Private Endpoints for the same Private Link service. Thus, it is possible to share these services with partners without exposing them to the internet.
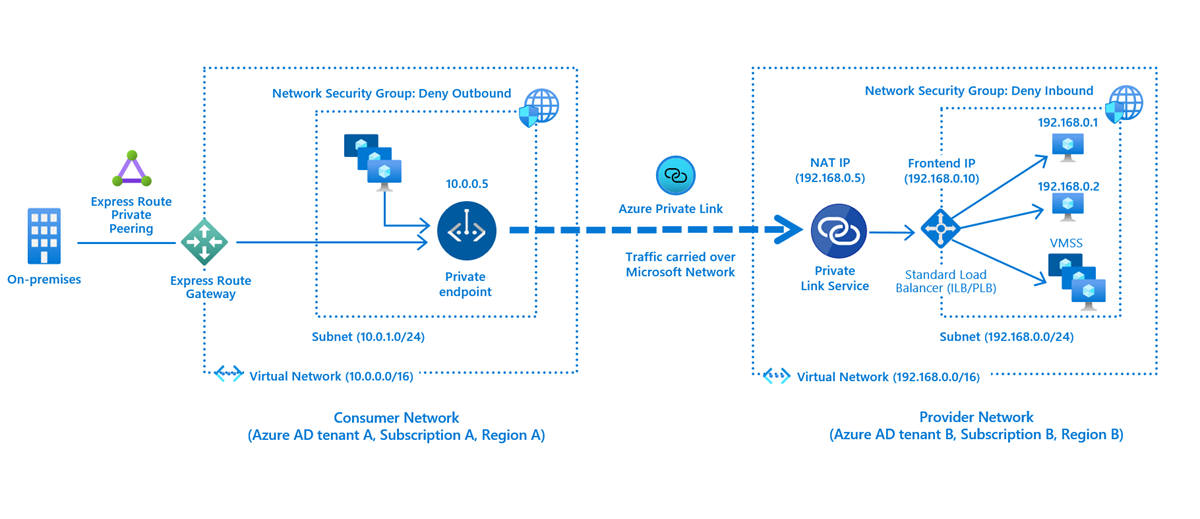
Private Endpoint for Azure App Service
The Private Endpoint is a NIC that gets assigned an IP from the VNet address range and connects securely to the App Service behind a Private Link. The Private Endpoint is used only for ingress. For egress, App Service has the VNet integration feature. Once the Private Endpoint is enabled, the public access to the App Service is disabled.
The Private Endpoint App Service feature is available for Premium V2, V3, and Functions Premium.
Choosing between ASE and App Service with Private Endpoint
The main drivers are tenant isolation, scalability, and cost. With the v3’s significantly reduced cost compared to the v2, ASE regains ground.
Tenant isolation
Both ASE and Private Endpoint offer network isolation, but ASE also provides a single-tenant environment which gives more control. With Private Endpoint, the AppService runs in the same multi-tenant environment.
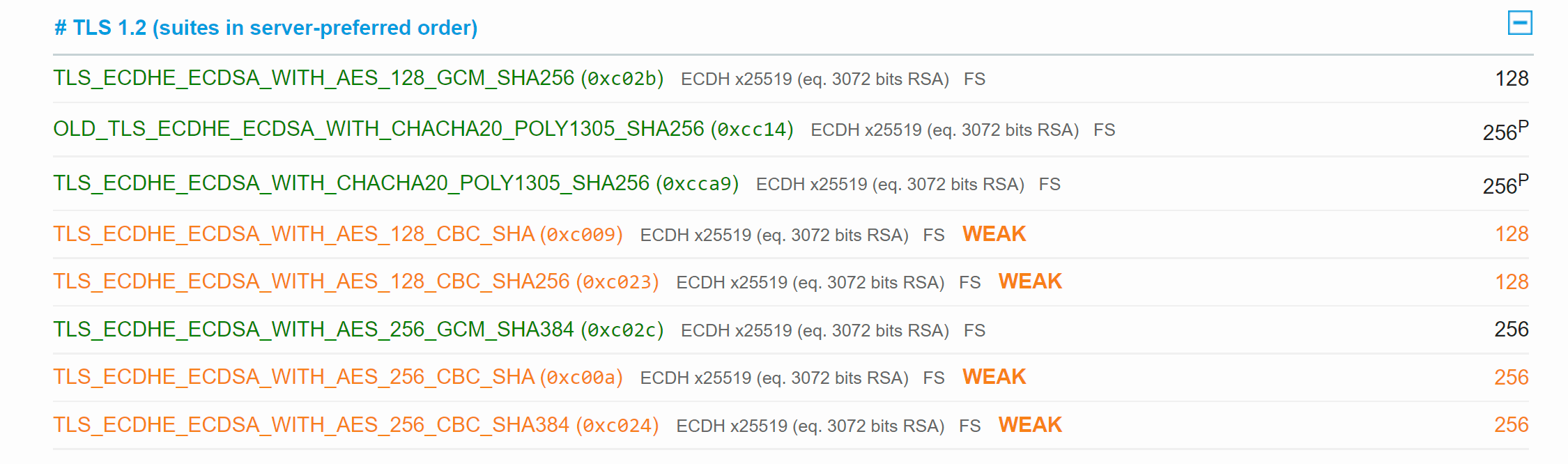
A quick scan of a multi-tenant App Service with SSL Labs will reveal that the App Service uses some weak ciphers for TLS 1.2. The ciphers are supported since they are still widely in use. The ASE comes with the same default cipher suite, but one of the dedicated environment perks is that it is possible to change it. That is not enabled for the multi-tenant App Service since it would affect the other tenants. The alternative is to use an Application Gateway or Azure Front Door that allows SSL settings configuration. But this, of course, applies only to internet-facing App Services. For intranet App Services, depending on the security requirements, it’s either the ASE or accepting the risk.
ASE v3 takes tenant isolation one step further and can be deployed on dedicated hardware.
Another multi-tenancy aspect is that the Private Endpoint needs to be created for each App Service, while with the ASE, this is external to the App Service configuration.
Scalability
As for scalability, a P3V3 tier for App Service has a maximum of 30 instances, while ASE v3 can have up to 200 App Service Plan instances to 200 individual App Service Plans, with any combination in between.
Scaling in ASE v3 is much faster than for v2 but not immediate like for the multi-tenant App Service.
Pricing
App Service Private Endpoint feature is available starting with Premium V2, which means a starting price of about 150$ per month. When comparing it with the starting cost of an ASE v2 of about 1450$, the Private Endpoint became a preferred choice when dealing with few LoB web apps. In ASE v3, there is no more stamp cost, and the starting price is now 420$.
If the App Service Premium tier meets the scalability and isolation requirements, the Private Endpoints feature will optimize the cost.
The following parts will delve more into topics such as networking, DevOps, and disaster recovery.